A friend of mine through Discord mentioned that they got their SecondLife avatar transformed into an ASCII text file on someone’s computer. Actually, they did that twice. It brought all kinds of fun ideas into my head about the implications of how an ASCII-transformation could be “locked”. Hence this post~
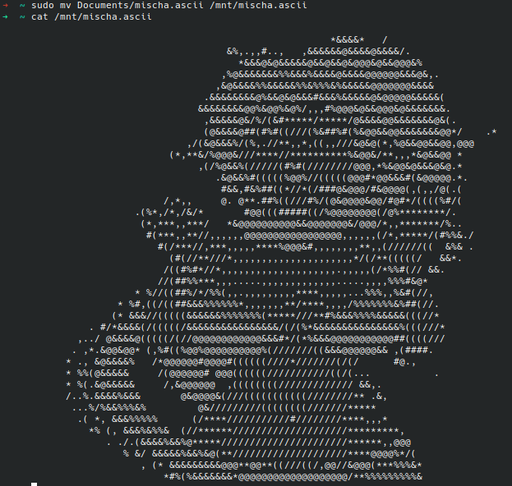
For this demonstration, I’ve picked up a random hard drive from my basement. It’s an 80GB Fujitsu 2.5in spinning-rust drive – but the size isn’t too important. ASCII is small.

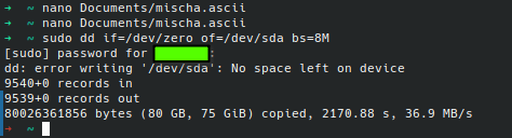
The next step is to zero out the drive. I want to make sure that my genie friend is the only thing on the drive (and that they have no means of escaping).
sudo dd if=/dev/zero of=/dev/sda bs=8M
Next, we want to make an encrypted filesystem. Encryption will do two things:
- Prevent the genie-imp’s file from being read
- Prevent the genie-imp’s file from being modified (unlocked)
In this case, I’m going to be mostly using the default options (except for a bigger default keysize for extra strength). (I’ll get to the mischa_keyfile part at the end.)
dd bs=512 count=4 if=/dev/random of=Documents/mischa_keyfile iflag=fullblock
cryptsetup luksFormat -s 512 /dev/sda Documents/mischa_keyfile
sudo cryptsetup luksOpen /dev/sda mischa_fs --key-file Documents/mischa_keyfile
Next up is creating the file system. Normally this would involve creating partitions first, but that isn’t necessary in this case because I’m only storing one file.
sudo mkfs.ext4 /dev/mapper/mischa_fs
sudo mount /dev/mapper/mischa_fs /mnt
Now we can move our genie-imp over to its new home.
But this isn’t enough. I want to take it a step further. So I encrypted Mischa at the file level as well. It prompts me for a password. I won’t spoil what I picked for obvious reasons~
sudo openssl aes-256-cbc -in /mnt/mischa.ascii -out /mnt/mischa.ascii.enc -pbkdf2
Of course, we want to verify that the Mischa is still readable if we decrypt it (to a temporary filesystem that is erased when I turn my computer off).
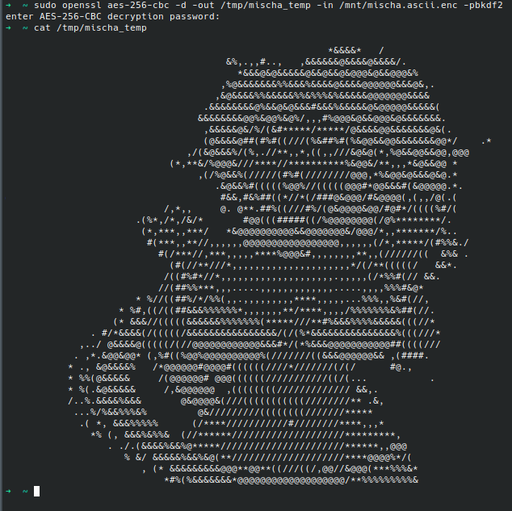
Unfortunately, this causes a small issue: we now have two Mischas. One is the encrypted one, and the other is unencrypted. To the unfamiliar, one might think that we can just delete the unencrypted version. But deleting doesn’t really delete the data. Instead, we need to overwrite it with random, useless data:
shred mischa.ascii
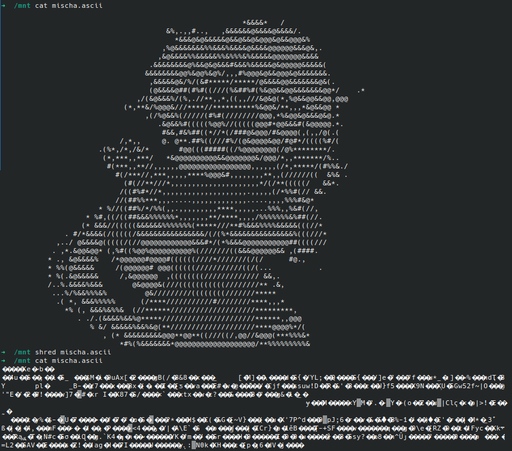
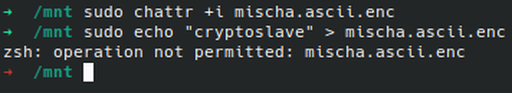
There’s one final, mostly unnecessary step to this process. There’s a special flag you can add to files that prevent changing them.
sudo chattr +i mischa.ascii.enc
Now I’ve safely returned the drive to the stack in my basement. I forgot to bring a marker to label it, but I’m sure I’ll remember it…. right?
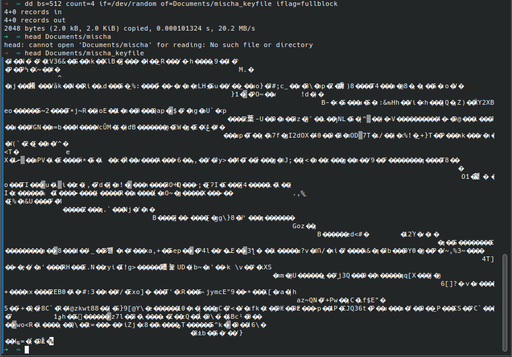
I mentioned that I’d get to the keyfile at the end. A keyfile is like a password, but in file form. They also tend to be much longer. Here’s me generating a random 2048-byte keyfile and reading the beginning of it:
Because of the extra length and randomness of this keyfile, losing it would mean that Mischa would be (effectively) permanently encrypted.


